JwtUtil
(이건 Spring Security 스펙은 아닙니다.)
package org.example.statelessspringsecurity.config;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import io.jsonwebtoken.security.Keys;
import jakarta.annotation.PostConstruct;
import lombok.extern.slf4j.Slf4j;
import org.example.statelessspringsecurity.enums.UserRole;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.stereotype.Component;
import org.springframework.util.StringUtils;
import java.security.Key;
import java.util.Base64;
import java.util.Date;
@Slf4j(topic = "JwtUtil")
@Component
public class JwtUtil {
private static final String BEARER_PREFIX = "Bearer ";
private static final long TOKEN_TIME = 60 * 60 * 1000L; // 60분
@Value("${jwt.secret.key}")
private String secretKey;
private Key key;
private final SignatureAlgorithm signatureAlgorithm = SignatureAlgorithm.HS256;
@PostConstruct
public void init() {
byte[] bytes = Base64.getDecoder().decode(secretKey);
key = Keys.hmacShaKeyFor(bytes);
}
public String createToken(Long userId, String email, UserRole userRole) {
Date date = new Date();
return BEARER_PREFIX +
Jwts.builder()
.setSubject(String.valueOf(userId))
.claim("email", email)
.claim("userRole", userRole.getUserRole())
.setExpiration(new Date(date.getTime() + TOKEN_TIME))
.setIssuedAt(date) // 발급일
.signWith(key, signatureAlgorithm) // 암호화 알고리즘
.compact();
}
public String substringToken(String tokenValue) {
if (StringUtils.hasText(tokenValue) && tokenValue.startsWith(BEARER_PREFIX)) {
return tokenValue.substring(7);
}
log.error("Not Found Token");
throw new NullPointerException("Not Found Token");
}
public Claims extractClaims(String token) {
return Jwts.parserBuilder()
.setSigningKey(key)
.build()
.parseClaimsJws(token)
.getBody();
}
}
SecurityConfig
(Spring Security 설정 파일이다.)
package org.example.statelessspringsecurity.config;
import lombok.RequiredArgsConstructor;
import org.example.statelessspringsecurity.enums.UserRole;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.method.configuration.EnableMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configurers.AbstractHttpConfigurer;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter;
@Configuration
@RequiredArgsConstructor
@EnableWebSecurity
@EnableMethodSecurity(securedEnabled = true)
public class SecurityConfig {
private final JwtSecurityFilter jwtSecurityFilter;
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
return http
.csrf(AbstractHttpConfigurer::disable)
.sessionManagement(session -> session
.sessionCreationPolicy(SessionCreationPolicy.STATELESS) // SessionManagementFilter, SecurityContextPersistenceFilter
)
.addFilterBefore(jwtSecurityFilter, SecurityContextHolderAwareRequestFilter.class)
.formLogin(AbstractHttpConfigurer::disable) // UsernamePasswordAuthenticationFilter, DefaultLoginPageGeneratingFilter 비활성화
.anonymous(AbstractHttpConfigurer::disable) // AnonymousAuthenticationFilter 비활성화
.httpBasic(AbstractHttpConfigurer::disable) // BasicAuthenticationFilter 비활성화
.logout(AbstractHttpConfigurer::disable) // LogoutFilter 비활성화
.authorizeHttpRequests(auth -> auth
.requestMatchers("/auth/signin", "/auth/signup").permitAll()
.requestMatchers("/test").hasAuthority(UserRole.Authority.ADMIN)
.anyRequest().authenticated()
)
.build();
}
}
JwtSecurityFilter
(기존의 Filter를 대체합니다.)
package org.example.statelessspringsecurity.config;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.ExpiredJwtException;
import io.jsonwebtoken.MalformedJwtException;
import io.jsonwebtoken.UnsupportedJwtException;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import lombok.NonNull;
import lombok.RequiredArgsConstructor;
import lombok.extern.slf4j.Slf4j;
import org.example.statelessspringsecurity.enums.UserRole;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.web.authentication.WebAuthenticationDetailsSource;
import org.springframework.stereotype.Component;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@Slf4j
@Component
@RequiredArgsConstructor
public class JwtSecurityFilter extends OncePerRequestFilter {
private final JwtUtil jwtUtil;
@Override
protected void doFilterInternal(
HttpServletRequest httpRequest,
@NonNull HttpServletResponse httpResponse,
@NonNull FilterChain chain
) throws ServletException, IOException {
String authorizationHeader = httpRequest.getHeader("Authorization");
if (authorizationHeader != null && authorizationHeader.startsWith("Bearer ")) {
String jwt = jwtUtil.substringToken(authorizationHeader);
try {
Claims claims = jwtUtil.extractClaims(jwt);
String userId = claims.getSubject();
String email = claims.get("email", String.class);
UserRole userRole = UserRole.of(claims.get("userRole", String.class));
if (userId != null && SecurityContextHolder.getContext().getAuthentication() == null) {
AuthUser authUser = new AuthUser(userId, email, userRole);
JwtAuthenticationToken authenticationToken = new JwtAuthenticationToken(authUser);
authenticationToken.setDetails(new WebAuthenticationDetailsSource().buildDetails(httpRequest));
SecurityContextHolder.getContext().setAuthentication(authenticationToken);
}
} catch (SecurityException | MalformedJwtException e) {
log.error("Invalid JWT signature, 유효하지 않는 JWT 서명 입니다.", e);
httpResponse.sendError(HttpServletResponse.SC_UNAUTHORIZED, "유효하지 않는 JWT 서명입니다.");
} catch (ExpiredJwtException e) {
log.error("Expired JWT token, 만료된 JWT token 입니다.", e);
httpResponse.sendError(HttpServletResponse.SC_UNAUTHORIZED, "만료된 JWT 토큰입니다.");
} catch (UnsupportedJwtException e) {
log.error("Unsupported JWT token, 지원되지 않는 JWT 토큰 입니다.", e);
httpResponse.sendError(HttpServletResponse.SC_BAD_REQUEST, "지원되지 않는 JWT 토큰입니다.");
} catch (Exception e) {
log.error("Internal server error", e);
httpResponse.sendError(HttpServletResponse.SC_INTERNAL_SERVER_ERROR);
}
}
chain.doFilter(httpRequest, httpResponse);
}
}
JwtAuthenticationToken
(기존의 Argument Resolver를 대체합니다.)
package org.example.statelessspringsecurity.config;
import org.springframework.security.authentication.AbstractAuthenticationToken;
public class JwtAuthenticationToken extends AbstractAuthenticationToken {
private final AuthUser authUser;
public JwtAuthenticationToken(AuthUser authUser) {
super(authUser.getAuthorities());
this.authUser = authUser;
setAuthenticated(true);
}
@Override
public Object getCredentials() {
return null;
}
@Override
public Object getPrincipal() {
return authUser;
}
}
JWT 방식에서 Spring Security 방식으로 변경시
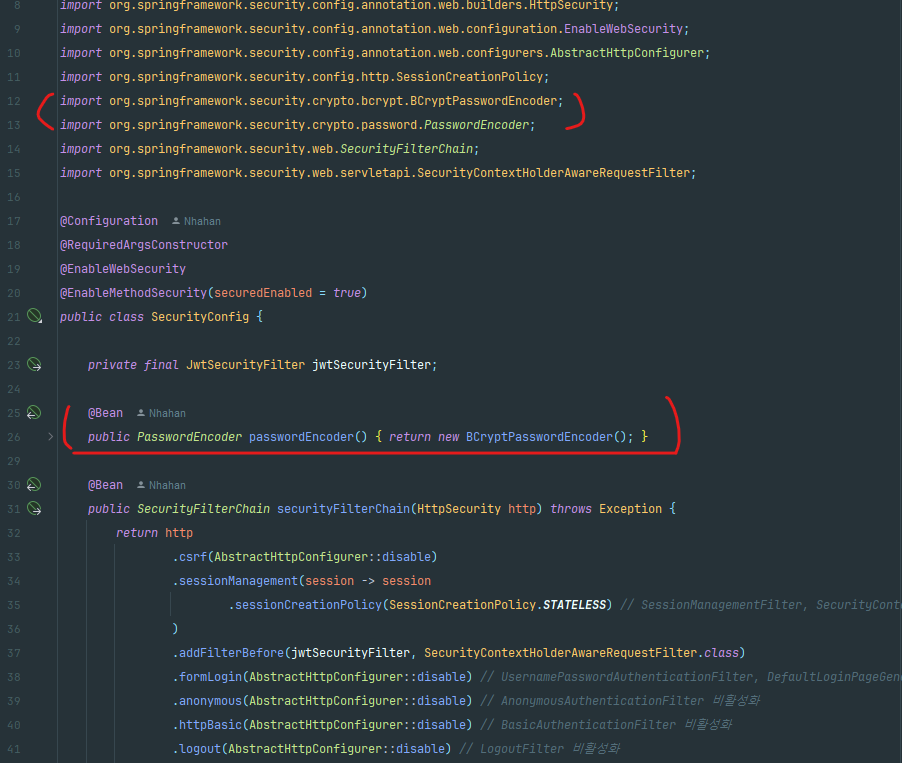
- Spring Security에 기본으로 PasswordEncoder 제공하기 때문에
: 기존에 만들어서 사용했던 PasswordEncoder를 만들필요 없이 밑의 사진처럼 SecurityConfig에 등록하면 된다.
- 이미지에 나와있는 것처럼 기존에 Argument Resolver 코드 중에 "resolveArgument"와 변경시JwtAuthenticationToken 코드 중 "getPrincipal"은 똑같다고 생각하면 된다.
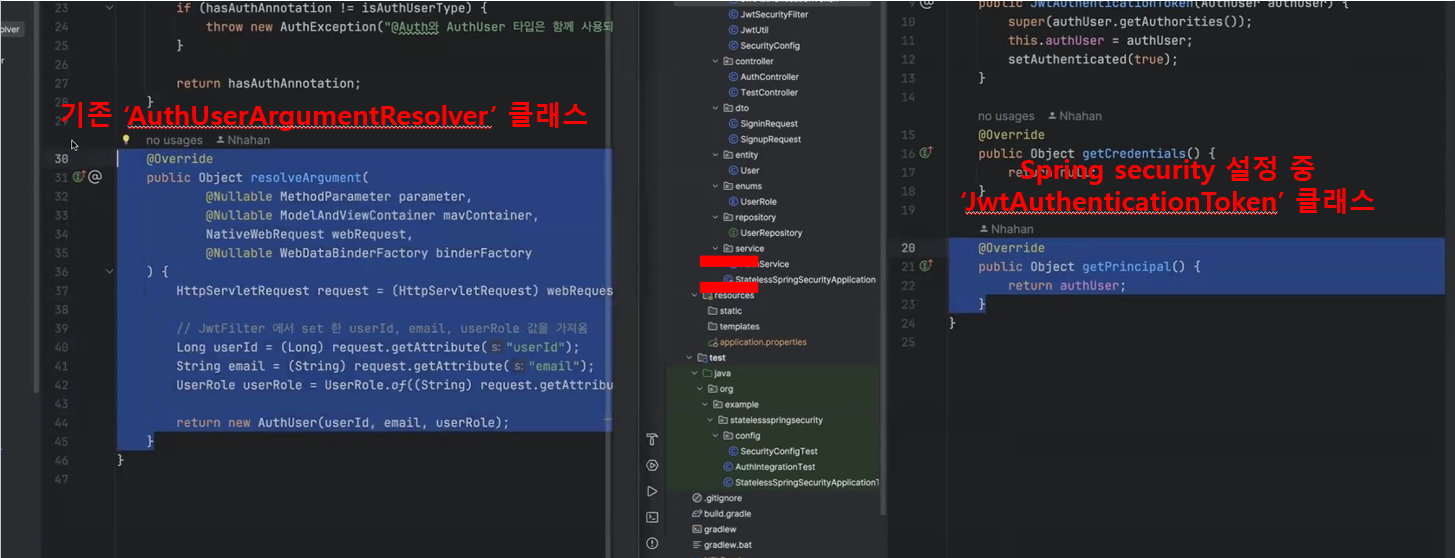
- 기존의 Argument Resolver를 대체했던 JwtAuthenticationToken파일에서 Object getPrincipal()메소드로 컴트롤러 파라미터에서 @AuthenticationPrincipal를 이용해 어떤 인증 객체를 받을 지 설정한다.
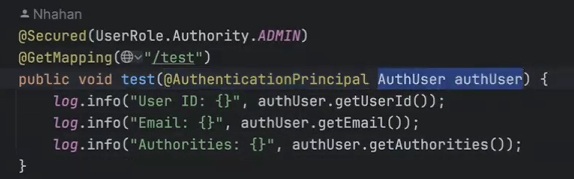
(밑의 이미지는 'authUser'를 받겠다고 설정한 것입니다.)

- SecurityConfig에서 권한 설정 방법이 2가지이다.
첫번째 방법
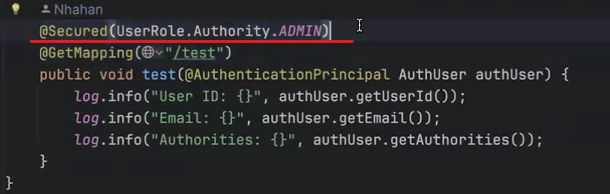
- 밑의 1번 이미지의 빨간색 밑줄친 부분처럼 설정한 후
- 밑의 2번 이미지처럼 컨트롤러에서 사용시 "@Secured"를 사용하여 권한 설정을 해준다.
(단, 이렇게 권한 설정하려고하면 3번의 이미지처럼 SecurityConfig에서 "@EnableMethodSecurity"를 붙여준다.)


두번째 방법
- SecurityConfig에서 한번에 권한 설정하는 방법이다.

'TIL(Today I Learned)' 카테고리의 다른 글
| [Spring Boot] 포스트맨으로 테스트하기 쉽게 환경변수 설정과 'Barere 접두사'를 제거한 순수한 토큰 헤더로 받기 (0) | 2024.10.25 |
|---|---|
| [Spring] QueryDSL 관련 코드 정리 (2) | 2024.10.10 |
| [CS스터디] Blocking I/O & Non-Blocking I/O (+ 동기와 비동기) (1) | 2024.09.29 |
| [내배캠] 아웃소싱 프로젝트 후 KPT 회고 작성 (0) | 2024.09.25 |
| [Java] Jwt Filter & 인증/인가 관련된 코드들 정리 (0) | 2024.09.11 |